How to Protect Customer Data from Cyberattacks
Customer data is information about customers obtained in a first-party context. Customers desire to be in control over their data because they do not trust how companies handle it.
.png) There are various publications utilized to assist businesses and government agencies with the most effective and up to date cybersecurity processes and procedures. The National Institute of Standards and Technology (NIST) has developed publications for cybersecurity and has become a widely accepted framework that outlines best practices, controls, methods, and common language to successfully implement a cybersecurity program. It has been implemented and adopted as the main framework throughout the United States government, United States partnering contracting agencies, private sectors, as well as on an international scale in countries such as Japan.
There are various publications utilized to assist businesses and government agencies with the most effective and up to date cybersecurity processes and procedures. The National Institute of Standards and Technology (NIST) has developed publications for cybersecurity and has become a widely accepted framework that outlines best practices, controls, methods, and common language to successfully implement a cybersecurity program. It has been implemented and adopted as the main framework throughout the United States government, United States partnering contracting agencies, private sectors, as well as on an international scale in countries such as Japan.
The NIST publications are broken into a variety of numbered sections for ease of organization and reference, all of which are tailored to different forms of business whether it be the private sector, public sector, government agencies, or generic inquiry. NIST 800-37 Rev 2 and NIST 800-53 Rev 5 are the primary two publications that outline the risk management framework that government agencies mandate compliance, as well as the many controls that must be implemented. Private corporations can voluntarily implement the tested methods but are not mandated and tend to follow the voluntary NIST Cybersecurity Framework (CSF) instead.
Under former President of the United States Barack Obama, an executive order was signed mandating certain cybersecurity functions for United States military and government entities, be applied and followed. This shift in cybersecurity mindset was highly encouraged for use in the private sector as well. The transparency and standards that were officially published by NIST helped create the NIST CSF compliance standards that private corporations utilize.
NIST CSF has a 7-step approach to help any entity bolster the cybersecurity program.
NIST Special Publication utilized in government sectors follow a similar path but instead utilize a 6-step Risk Management Framework (RMF) life cycle approach and use names such as Families and Controls rather than Categories and Subcategories. NIST Special Publication 800-37 Revision 2 is a lifecycle approach for applying a risk management framework to federal systems. Although this publication does exist specifically for federal systems, the methods can be translated into the private sector and is considered one of the NIST compliance frameworks.
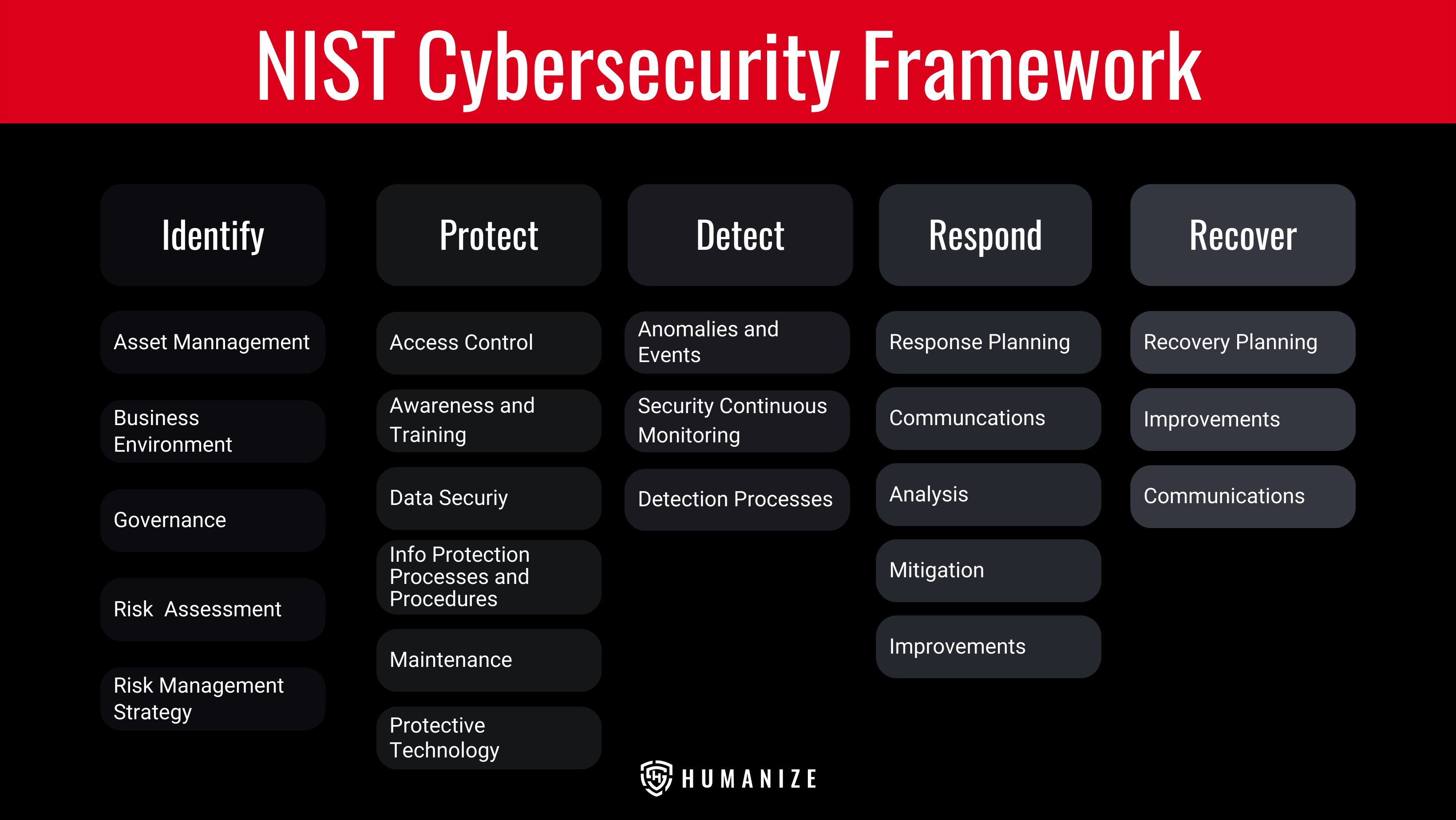
NIST CSF is a subset of NIST Special Publication 800-53 and was written with ISO 27001 in mind. This publication outlines all the necessary controls and compliance checklists that need to be implemented for the development and security of information systems. The controls vary but yet all focus on the confidentiality, integrity, and availability (CIA) triad for ultimate protection. NIST Special Publication 800-53 Revision 5 has over 1000 individual controls and meets all requirements for the Federal Information Security Management Act (FISMA).
The purpose of NIST CSF is to not make extra work, but rather to provide guidance and awareness on how corporations can implement methods to reduce Information Technology (IT) risk and network infrastructure disruption due to a malicious cyber threat. NIST CSF is created for reference to best practices, guidelines, standards, and actions that can be implemented for maximum protection against cyberattacks.
To be compliant under NIST standards on the federal government side, the organization must first undergo and pass an audit performed by an independent verification and validation team. This team goes through the organization's cybersecurity program to include all documentation, accesses, personnel, training, policy and technical aspects. Because NIST cybersecurity practices are voluntary for the private sector, the continuous monitoring and self-assessments performed on an annual basis will be an internal organizational reflection and those conducting the assessment will determine if the cybersecurity program is a success.
Cybersecurity is a continuous lifecycle, no matter which cybersecurity standard a corporation chooses to follow. Due to the evolving vulnerabilities and cyberthreats every day, businesses need to be constantly reviewing the cybersecurity risks that could affect the information systems and compromise sensitive data.