Challenges of Cybersecurity Board Reporting
Many chief information security officers (CISOs) find the prospect of reporting on cybersecurity to the board of directors daunting.
The Zero-Trust concept refers to the practice of verifying every entity attempting to access protected network resources from within or outside the network's perimeter, whether it is a human user, a bot, a device, or others. It reduces vulnerability of network to cyberattacks and ransomware by granting the privileges necessary to carry out a given task.
Zero Trust is a security strategy built on the concept of "never trust, always verify" to safeguard modern environments through robust authentication methods, network segmentation, and simplification of granular "least access" policies. Read on to learn about Zero-Trust Architecture and the seven components that make it up.
Zero-Trust Strategy has been adopted vastly, and more companies are moving to zero trust cybersecurity model. While conventional cybersecurity measures focus on coordinating with one another to protect an organization, the Zero-Trust Security model offers a more comprehensive framework for deciding where and how to implement security measures.
Keep reading to find out what a zero-trust architecture is and its seven pillars.
Though some deem it to be a philosophy rather than a cybersecurity strategy, Zero Trust model is an approach to cybersecurity meant to take over the traditional perimeter that adapts implicit trust.
Zero Trust model secures organizations by eliminating implicit trust. It treats all traffic, including those inside the organization’s network, as hostile until the pre-set attributes confirm them. The validation process happens by applying a based-on-context security policy, including the user’s role, location, device, and the requested data.
Access controls are set up through only approved IP addresses, ports, and protocols by validating trusted requests inside the network and blocking any inappropriate access.
Microsoft reported that 96% of cybersecurity decision-makers consider Zero Trust essential to their company’s future success. What is the big deal about Zero-Trust Architecture, though? Below is a quick demonstration of Zero Trust model’s most advantageous features and benefits:
Organizations embrace the zero-trust model for different purposes, like reducing the risk of insider threats, securing the remote workforce, preserving customer privacy, and protecting their cloud infrasturcture.
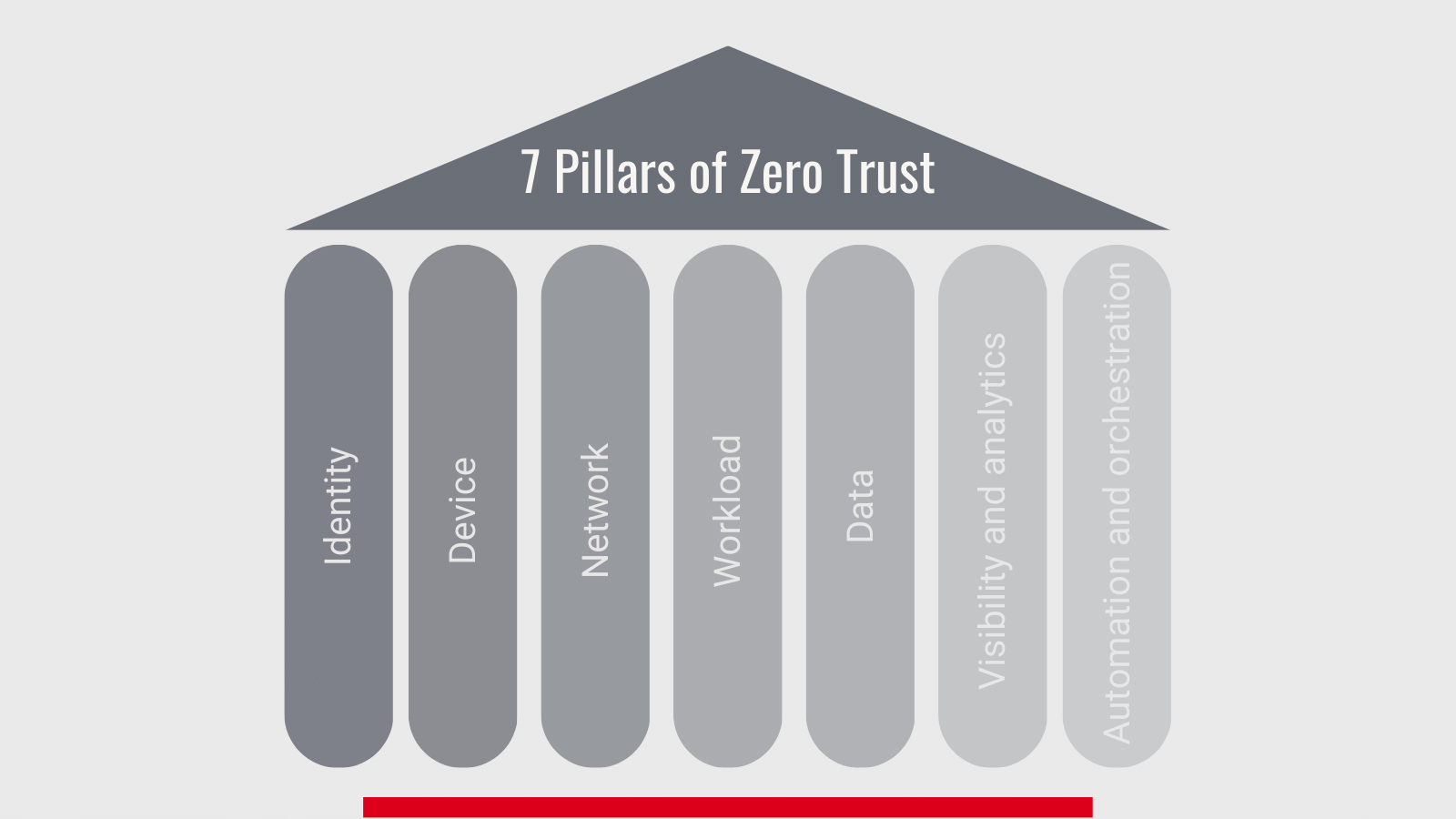 Before implementing Zero-Trust Architecture, businesses need to consider seven main pillars that support a Zero-Trust Architecture. The CISA zero trust model Maturity model, developed by the Cybersecurity and Infrastructure Security Agency (CISA), identifies the following as the foundational pillars of a Zero Trust Model.
Before implementing Zero-Trust Architecture, businesses need to consider seven main pillars that support a Zero-Trust Architecture. The CISA zero trust model Maturity model, developed by the Cybersecurity and Infrastructure Security Agency (CISA), identifies the following as the foundational pillars of a Zero Trust Model.
Identity is an essential part of a Zero-Trust Architecture. Users’ identities must be dynamically confirmed before accessing the requested resources to ensure high levels of identity security. Organizations use passwords along with multi-factor authentication to mitigate the cyber threats.
Organizations need to identify the devices being used to access their resources to ensure that these are authorized devices as long as they align with their compliance mechanisms.
Sensitive resources are micro-segmented to secure these resources from unauthorized access. Organizations deploy the needed protections that enable them to know what is on the network.
An organization’s workload includes the applications, processes, and programs used for operational purposes. Securing the workload is essential to prevent unauthorized access involving stealing and collecting sensitive data and tampering with it.
Organizations should protect their data on devices, applications, or networks. To do so, data is organized and categorized, so it is accessible only for the relevant categories of the users. Also, organizations use other protection mechanisms like encrypting data while it is in transit and at rest to protect it from exfiltration threats.
Organizations need to monitor all security processes continuously. Thus, these processes are automated using artificial intelligence to detect divergences, monitor access control and data visibility.
Automation and orchestration form an essential part of deploying a Zero-Trust Architecture. Modern ways, including the AI technique, are applied to automate and control the entire Zero-Trust model across the organization’s systems.
All in all, the transition to adopting Zero Trust model is an effective framework to increase cybersecurity and prevent compromising organizations’ highly sensitive resources. These seven pillars constitute the cornerstone of a Zero-Trust strategy.