How to Develop a Cybersecurity Strategy for 2024: 7 Key Steps for Effective Protection
Explore the 7 key steps to craft a robust cybersecurity strategy for 2024. Learn to assess risks, implement technologies, and train your team for top defense.

In the realm of cybersecurity, the manipulation of security loopholes and exposed vulnerabilities remains a prevalent cause of cyberattacks. Many businesses unwittingly have exposed unprotected data and inadequate cybersecurity resources, posing a substantial risk.
The global cyber security market reached a value of about USD 236.75 billion in 2023, according to Expert Market Research. Projections indicate a steady growth rate of about 8.8% from 2024 to 2032, ultimately reaching a value of approximately USD 506.79 billion by 2032. In a concerning trend, global cyberattacks surged by 7% in the first quarter of 2023 compared to the previous year, with each company enduring an average of 1248 attacks per week during this period, as reported by Infosecurity Magazine.
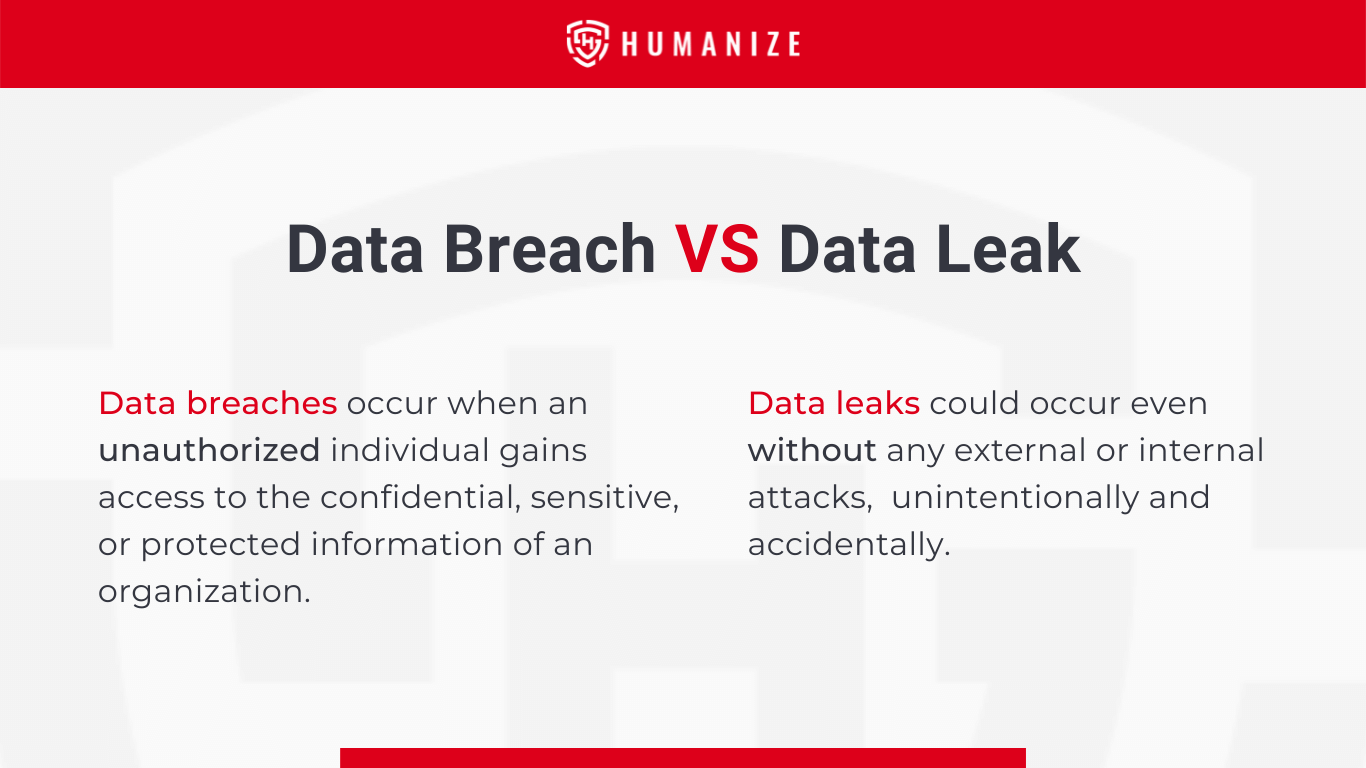
A data breach occurs when an unauthorized individual gains access to an organization's confidential, sensitive, or protected information, which is then accessed and disseminated without proper authorization. The repercussions of a data breach can be significant, affecting individuals, large corporations, and even governmental bodies.
Data leaks could occur even without any external or internal attacks. Someone may discover a flaw that already exists within the system and exploit it, intentionally or unintentionally. Conversely, an organization may have mishandled its data and had it hacked because of weak information security policies. There are many recent cases of accidental or unintentional data leaks. The most well-known recent data leak case was the MOVEit data breach, first reported in June 2023. MOVEit is a file transfer tool used by a wide range of organizations, including government agencies, educational institutions, and businesses. The breach affected over 200 organizations and up to 17.5 million individuals.
Most of the regular cases of data leaks that we usually see on the news occur due to the system vulnerabilities of an enterprise itself rather than from an external attack. Data breaches, on the other hand, are frequently the outcome of a cybercriminal's intention to get access to sensitive information.
However, data leaks may later result in data breaches. Suppose cyber attackers discover a major loophole or a way to exploit the system of an organization. In that case, it might provide them with all the information and resources they need to execute a large-scale data breach successfully.
Both result in similar consequences: whether it was due to a breach or a leak, the organization's data has been compromised. Account takeovers and even identity theft might occur because of stolen data. The next step is to make sure that any information that was taken cannot be utilized against the data owner. For example, if your banking information has been hacked, you may want to put your account or card on hold until you take the necessary measures to protect yourself.
Data Breaches: Common causes include the absence of a robust information security policy, compromised vulnerabilities, outdated firewalls, the use of outdated devices, and poorly configured networks.
Data Leaks: Data leaks often happen inadvertently and often bypass a company's security policies. These leaks can result from employee mistakes, such as falling for tactics like phishing emails.
The human element is the weakest point in any information security measure. Employees and staff often tend to get easily manipulated and fall victim to social engineering (phishing emails), malware, and so on, which later results in the breach of confidential data and information.
Customers trust businesses with their sensitive information because they believe they will secure it with appropriate security measures. A powerful reputation is frequently a company's most significant asset since an enterprise always strives to create and preserve its existing brand's integrity. One small event, such as a data leak, may, however, damage even the most enviable of reputations. Therefore, it is important not to overlook any exposed vulnerabilities within the system.
An organization needs to identify which of its assets are the most valuable. In this way, it can limit the authority over those resources by only assigning the trusted and the responsible personnel.
Most of the attackers plan their attacks, focusing on the weakest points of an organization, which are the employees. All the employees of an organization must be trained and made aware of all the possible threats and risks.
Use of easily guessable or simple passwords such as birthdates, names of pets, or any form of frequently used words should be avoided. There should be a specific format of passwords that are long and should contain letters with upper and lower cases, special characters, and numbers as well.
While no security measures can guarantee 100% protection, regular cybersecurity procedures can significantly reduce the risk of potential threats. These measures demonstrate an organization's commitment to safeguarding clients' confidential information and enable swift action according to established online security policies in the event of an incident.
Prevent data breaches and data leaks with Humanize Salience. Book a free demo today.